- Forum
- Deobfuscating with Calc.exe
For those who are familiar with the feature [literals], you might be surprised at how easily this is undone. As the title says, calc.exe - that is, the default Windows calculator - is capable to deobfuscate the literals by simply copy-pasting the whole line of mathematical operations. That is if all are literals (and not identifiers, function calls, etc)
Example
To solve the local a = ((16164 + (((3864 + 364101) - 274396) - 67600)) + (190952 - 110638)) from the local demo we simply copy the ((16164 + (((3864 + 364101) - 274396) - 67600)) + (190952 - 110638)), which are all valid mathematical operations, and past them, in our default Windows calculator as shown below.
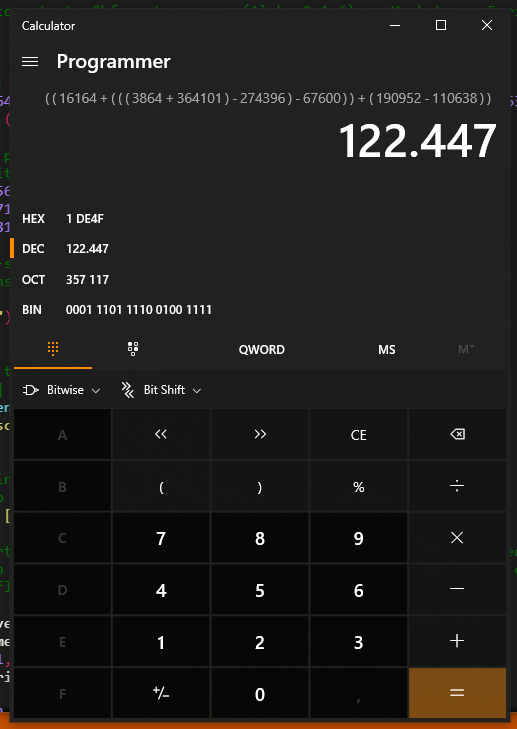
Tada, the value hidden underneath those operations is 122447
Solution
To harden against basic attacks like these we might want to add some extra flavors to the mix. That's why Mixed Boolean Arithmetics (MBA's) have been added into Alpha v0.1.6!
To elaborate more on what MBAs are, they are simply replacing basic arithmetic operations such as A + B into something like (A & B) + (A | B). However, this is Lua and we can't just do bitwise operations like this. Instead, it will be more like bit32.band(A, B) + bit32.bor(A, B). These will be even more fun to deobfuscate as we can perform string obfuscation on "band" and "bor" lookup. Just keep in mind these bitwise calls add some extra overhead.
The feature can be used with the [MBAv1] button under the "All Obfuscation" tab, enjoy!